Leveraging PFSense Nat Rules to redirect DNS requests when the device itself won’t let you
This is a continuation of posts on Network Security
In the last post I explained how to disable IPv6 on PFSense and then completely stop traffic logged after disabling IPv6 on PFSense.
In this post I’ll show you how to redirect DNS requests to your preferred DNS provider. Note that this does not include DNS over HTTPS (DoH) requests which I simply block.
Maybe I’ll write about more about DoH later.
NAT Port Forward to Overcome Hardcoded DNS Servers
One of the things that really annoys me with some IoT and Wi-Fi devices is that they will not let you redirect DNS to your preferred DNS servers. I wrote about why I like to use CloudFlare’s DNS here:
Easy DNS Change To Prevent Attacks
I can usually force these devices into using the DNS server I want to use by creating NAT rules on PFSense to redirect any DNS traffic to alternate servers to go to CloudFlare.
To configure a NAT rule for this purpose navigate to:
> Firewall > NAT
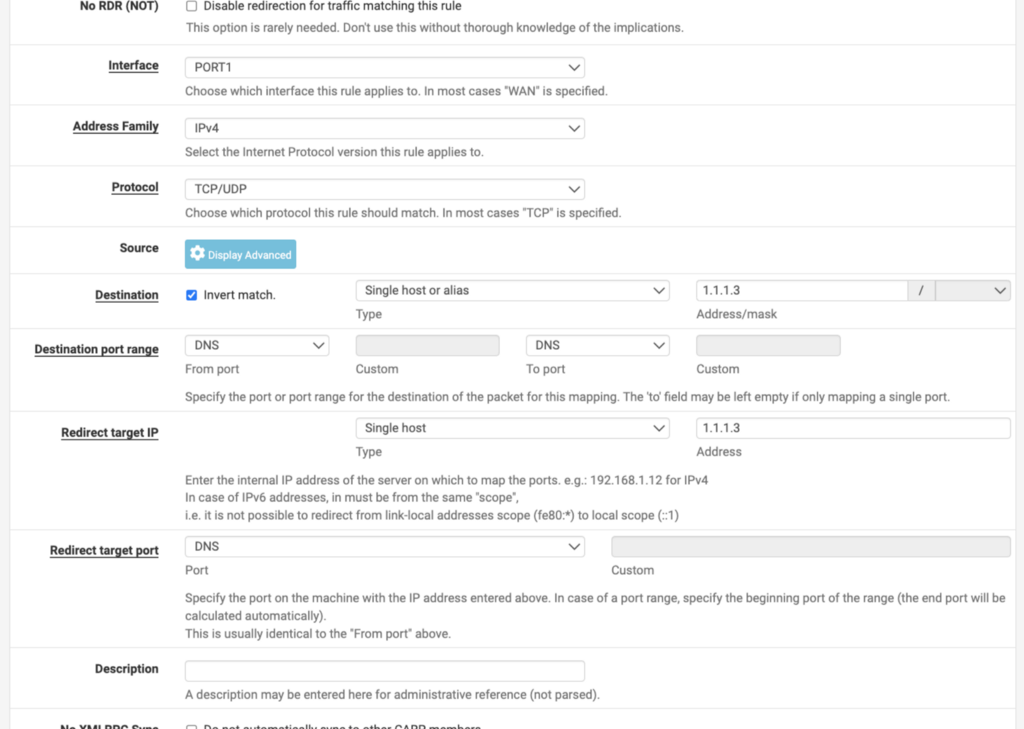
Here’s an example of how I configure that rule for a particular port I named PORT1:
I’ve seen problems and attacks on DNS forwarders and resolvers and I’d rather divvy up the DNS portion of networking to go straight to CloudFlare and let my Firewall handle other things. I don’t resolve DNS for devices using my firewall, though that could reduce traffic destined for the Internet.
I can use a similar approach to redirect annoying ICMP traffic that constantly sends pings over the Internet by redirecting that traffic to my firewall instead and allowing it to respond.
These rules might not work if a vendor is specifically trying to reach their own servers, but in most cases it’s just a simple device trying to figure out if it’s connected to the Internet or not or resolve domain names. Why these hosts need to be hard-coded to particular DNS servers is not clear to me. They could just use DHCP and whatever DNS name is provided by the local network, but in any case, this resolves the issue 99% of the time so I can create fewer firewall rules and have a less complex network.
Follow for updates.
Teri Radichel
If you liked this story please clap and follow:
******************************************************************
Medium: Teri Radichel or Email List: Teri Radichel
Twitter: @teriradichel or @2ndSightLab
Requests services via LinkedIn: Teri Radichel or IANS Research
******************************************************************
© 2nd Sight Lab 2022
____________________________________________
Author:
Cybersecurity for Executives in the Age of Cloud on Amazon
Need Cloud Security Training? 2nd Sight Lab Cloud Security Training
Is your cloud secure? Hire 2nd Sight Lab for a penetration test or security assessment.
Have a Cybersecurity or Cloud Security Question? Ask Teri Radichel by scheduling a call with IANS Research.
Cybersecurity & Cloud Security Resources by Teri Radichel: Cybersecurity and Cloud security classes, articles, white papers, presentations, and podcasts
Redirect IoT Devices to Preferred DNS was originally published in Cloud Security on Medium, where people are continuing the conversation by highlighting and responding to this story.