Every week seems to bring news of another data breach, and it’s no surprise why: securing sensitive data has become harder than ever. And it’s not just because companies are dealing with orders of magnitude more data. Data flows and user roles are constantly shifting, and data is stored across multiple technologies and cloud environments. Not to mention, compliance requirements are only getting

- January 20, 2025
- by Francis Schmuff
- Cyber News
- Less than a minute
- 160 Views
Related Post
- by Francis Schmuff
- August 10, 2025
New Win-DDoS Flaws Let Attackers Turn Public Domain
A novel attack technique could be weaponized to rope thousands of public domain controllers (DCs) around the world to create
- by Francis Schmuff
- August 10, 2025
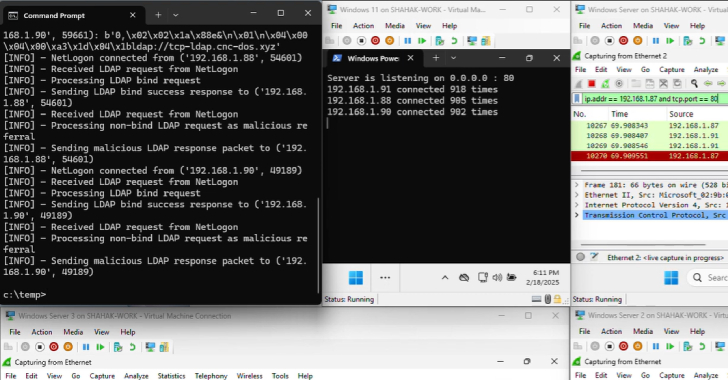
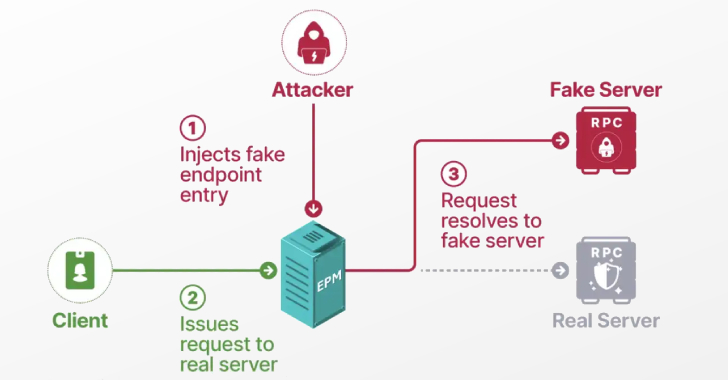
Researchers Detail Windows EPM Poisoning Exploit Chain Leading
Cybersecurity researchers have presented new findings related to a now-patched security issue in Microsoft’s Windows Remote Procedure Call (RPC) communication
- by Francis Schmuff
- August 9, 2025
Linux-Based Lenovo Webcams’ Flaw Can Be Remotely Exploited
Cybersecurity researchers have disclosed vulnerabilities in select model webcams from Lenovo that could turn them into BadUSB attack devices. “This
- by Francis Schmuff
- August 9, 2025
Researchers Reveal ReVault Attack Targeting Dell ControlVault3 Firmware
Cybersecurity researchers have uncovered multiple security flaws in Dell’s ControlVault3 firmware and its associated Windows APIs that could have been