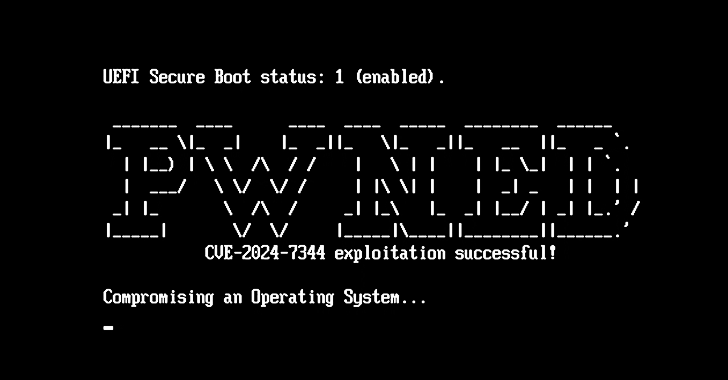
Details have emerged about a now-patched security vulnerability that could allow a bypass of the Secure Boot mechanism in Unified Extensible Firmware Interface (UEFI) systems.
The vulnerability, assigned the CVE identifier CVE-2024-7344 (CVSS score: 6.7), resides in a UEFI application signed by Microsoft’s “Microsoft Corporation UEFI CA 2011” third-party UEFI certificate, according to a new