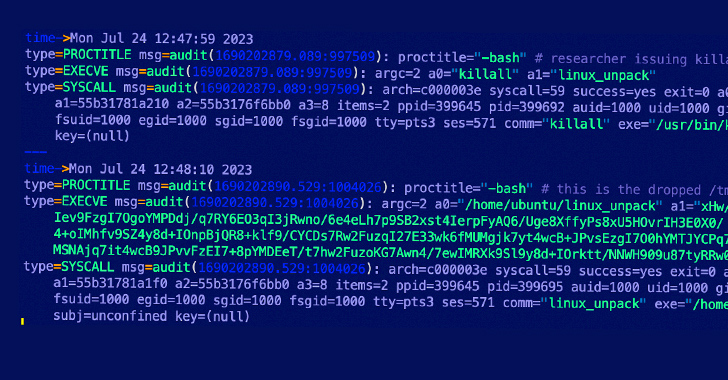
The P2PInfect peer-to-peer (P2) worm has been observed employing previously undocumented initial access methods to breach susceptible Redis servers and rope them into a botnet.
“The malware compromises exposed instances of the Redis data store by exploiting the replication feature,” Cado Security researchers Nate Bill and Matt Muir said in a report shared with The Hacker News.
“A common attack