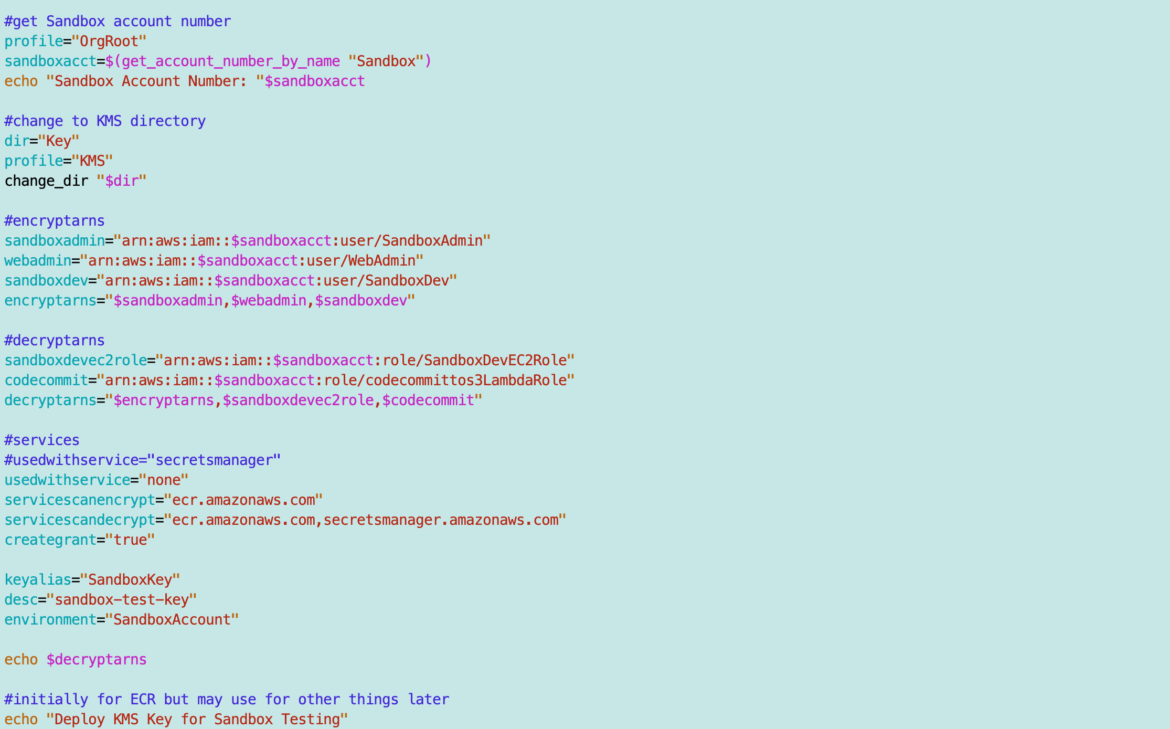
ACM.358 A common template for key deployment that includes organization and environment names — logs, deploy, and appdata keys
- October 31, 2023
- by
- Cyber News, Cyber Threat Trends
- Less than a minute
- 317 Views
Related Post
- by Francis Schmuff
- August 6, 2025
Ransomware plunges insurance company into bankruptcy
Collapsed company’s founder says that its fortunes were hampered by the refusal of authorities to release the criminals’ seized funds
- by Francis Schmuff
- August 6, 2025
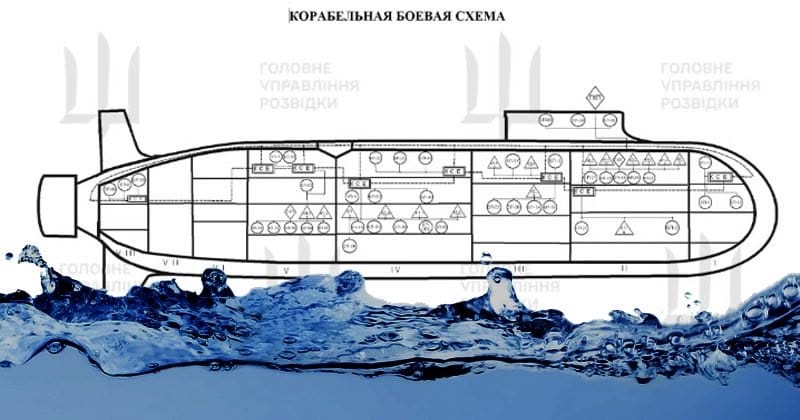
Ukraine claims to have hacked secrets from Russia’s
Ukraine’s Defence Intelligence agency (HUR) claims that its hackers have successfully stolen secret files and classified data on a state-of-the-art
- by Francis Schmuff
- August 6, 2025
Who Got Arrested in the Raid on the
On July 22, 2025, the European police agency Europol said a long-running investigation led by the French Police resulted in
- by Francis Schmuff
- August 6, 2025
AI Slashes Workloads for vCISOs by 68% as
As the volume and sophistication of cyber threats and risks grow, cybersecurity has become mission-critical for businesses of all sizes.