A total of roughly 100,000 people had their personal data stolen during the cyber-attack
- December 13, 2022
- by
- Cyber News, Cyber Threat Trends
- Less than a minute
- 232 Views
Related Post
- by Francis Schmuff
- April 16, 2025
Funding Expires for Key Cyber Vulnerability Database
A critical resource that cybersecurity professionals worldwide rely on to identify, mitigate and fix security vulnerabilities in software and hardware
- by Francis Schmuff
- April 15, 2025
RansomHouse ransomware: what you need to know
What is RansomHouse? RansomHouse is a cybercrime operation that follows a Ransomware-as-a-Service (RaaS) business model, where affiliates (who do not
- by Francis Schmuff
- April 16, 2025
Chinese Android Phones Shipped with Fake WhatsApp, Telegram
Cheap Android smartphones manufactured by Chinese companies have been observed pre-installed with trojanized apps masquerading as WhatsApp and Telegram that
- by Francis Schmuff
- April 16, 2025
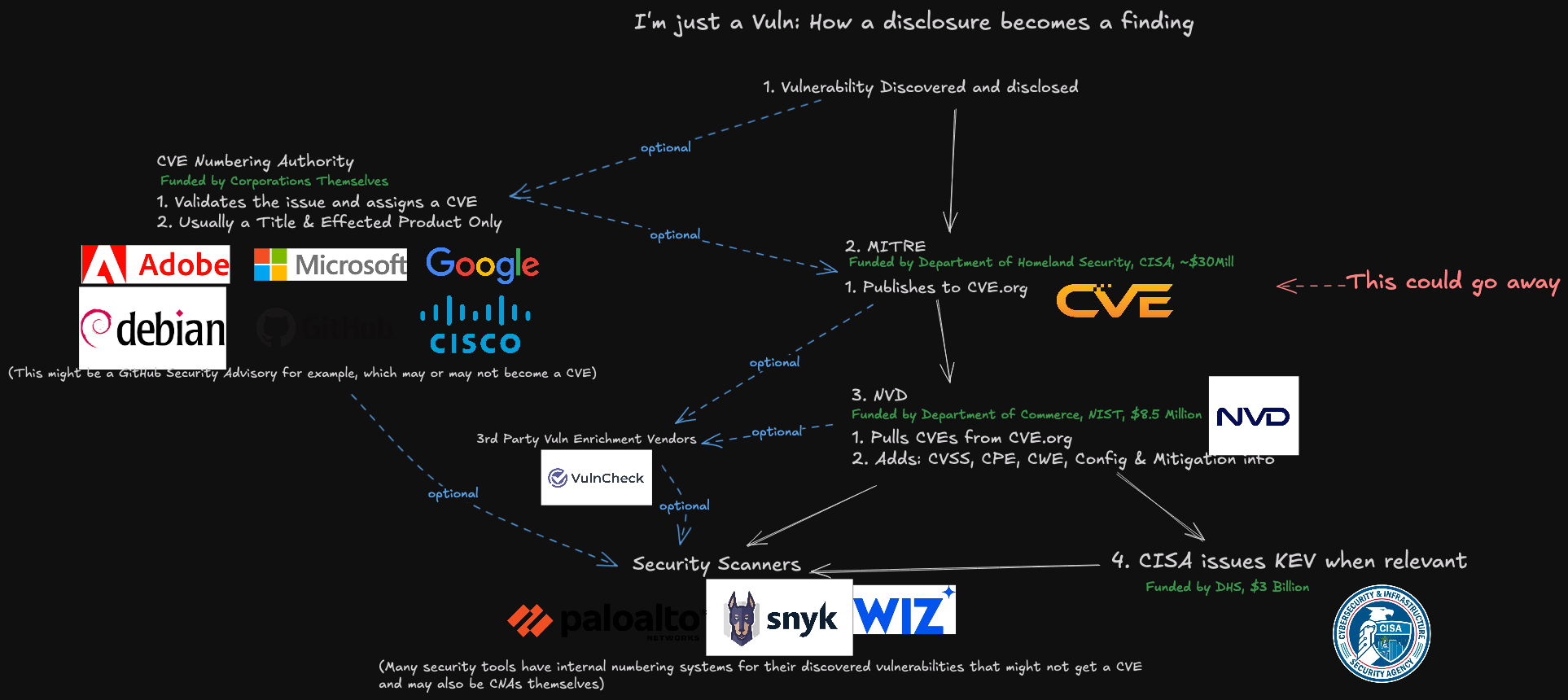
U.S. Govt. Funding for MITRE’s CVE Ends April
The U.S. government funding for non-profit research giant MITRE to operate and maintain its Common Vulnerabilities and Exposures (CVE) program
- by Francis Schmuff
- April 16, 2025
Funding Expires for Key Cyber Vulnerability Database
A critical resource that cybersecurity professionals worldwide rely on to identify, mitigate and fix security vulnerabilities in software and hardware
- by Francis Schmuff
- April 15, 2025
RansomHouse ransomware: what you need to know
What is RansomHouse? RansomHouse is a cybercrime operation that follows a Ransomware-as-a-Service (RaaS) business model, where affiliates (who do not
- by Francis Schmuff
- April 16, 2025
Chinese Android Phones Shipped with Fake WhatsApp, Telegram
Cheap Android smartphones manufactured by Chinese companies have been observed pre-installed with trojanized apps masquerading as WhatsApp and Telegram that
- by Francis Schmuff
- April 16, 2025
U.S. Govt. Funding for MITRE’s CVE Ends April
The U.S. government funding for non-profit research giant MITRE to operate and maintain its Common Vulnerabilities and Exposures (CVE) program