What’s happened?
Researchers at Abnormal have discovered the latest evolution in call-back phishing campaigns.
Call-back phishing?
Traditional phishing emails might contain a malicious link or attachment, and lure recipients into clicking on them via social engineering techniques.
Call-back phishing dupes unsuspecting victims into telephoning a fraudulent call centre, where they will speak to an actual human being – who will then trick them into downloading and running malware, providing malicious hackers with remote access to their PC.
How would I be tricked into calling a bogus call centre?
It’s probably easier than you imagine. You may know the real website addresses of services like PayPal, Norton, GeekSquad, or Disney+, but do you know the phone number for their support desk?
So all a malicious hacker has to do is send me an email from a service I use, giving me a compelling reason to call them…
…and maybe you will just call the number in the email.
Here’s an example where a fraudulent email claiming to come from PayPal claims that Netflix has charged you almost $500. If you don’t recognise the transaction, you’re invited to call a support number.
Okay, I can see how that might work on some people. But surely I could just look at the email headers and determine it’s not really from the company it claims to be from.
Well yes, you might… if you’re nerdy enough to check your emails with that much dedication. But most people wouldn’t ever bother doing that.
And furthermore, the latest attacks are exploiting Google Forms in a rather ingenious way to make their call-back phishing emails even more believable.
Ingenious?
I think so.
Here’s what appears to be happening behind the scenes in the latest BazarCall (also known as BazaCall) attacks seen by Abnormal’s security researchers.
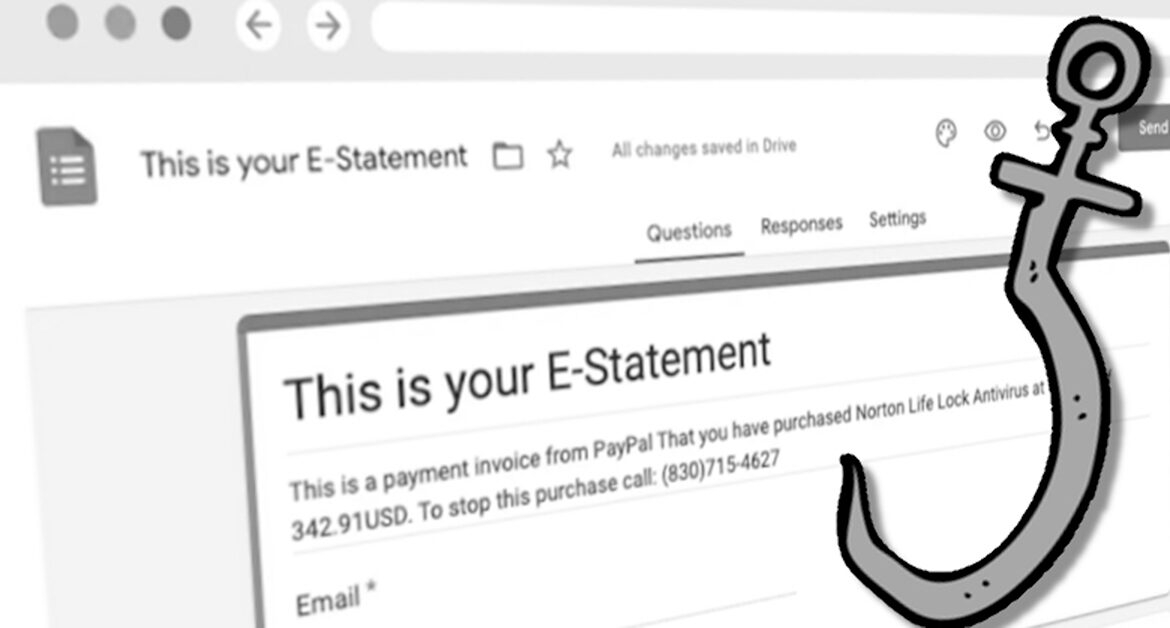
The first step is that the attackers creates a bogus statement in Google Forms, containing thanks for payment, and telling the reader to call a number if they wish to stop the purchase.
Next, the attacker changes the form’s settings to automatically send a copy of the completed form to any email address entered into the form.
Then, and this is where things really begin to get clever, the attacker sends an invitation to complete the form to themselves, not to their intended victim.
So, the attacker receives the invitation to fill out the form – and when they complete it, they enter their intended victim’s email address into the form, not their own.
Ah! So, the victim receives the statement, telling them to call a number if they want to dispute the charges.
Right!
But I don’t see how this is any better for the attacker than just sending the victim a call-back phishing email directly. Why mess around with Google Forms?
The attackers are taking advantage of the fact that the emails are being sent out directly by Google Forms (from the google.com domain). It’s an established legitimate domain that helps to make the email look more legitimate and is less likely to be intercepted en route by email-filtering solutions.
That’s really sneaky.
Isn’t it? And that’s why businesses and individuals should be on their guard – and think twice before calling customer support call centres. Are you sure you’re calling a real support centre, or could it be an operation run by cybercriminals?
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor and do not necessarily reflect those of Tripwire