Counterfeit Facebook pages and sponsored ads on the social media platform are being employed to direct users to fake websites masquerading as Kling AI with the goal of tricking victims into downloading malware.
Kling AI is an artificial intelligence (AI)-powered platform to synthesize images and videos from text and image prompts. Launched in June 2024, it’s developed by Kuaishou Technology, which is headquartered in Beijing, China. As of April 2025, the service has a user base of more than 22 million, per data from the company.
“The attack used fake Facebook pages and ads to distribute a malicious file which ultimately led to the execution of a remote access Trojan (RAT), granting attackers remote control of the victim’s system and the ability to steal sensitive data,” Check Point said.
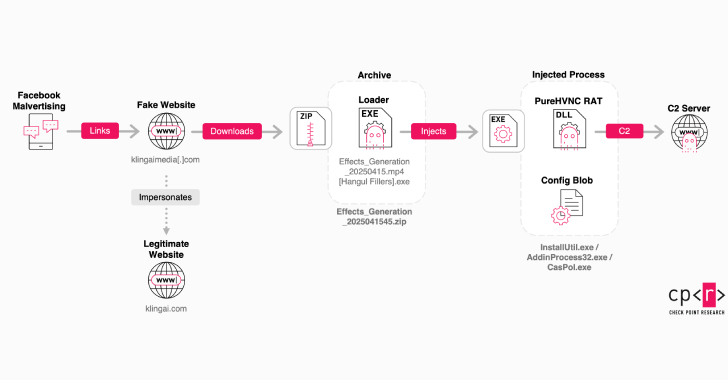
First detected in early 2025, the campaign leads unsuspecting users to a spoofed website such as klingaimedia[.]com or klingaistudio[.]com, where they are asked to create AI-generated images or videos directly in the browser.
However, the website does not generate the multimedia count as advertised. Rather, it offers the option to a purported image or video that, in reality, is a malicious Windows executable hidden using double extensions and Hangul Filler (0xE3 0x85 0xA4) characters.
The payload is included in a ZIP archive and acts as a loader to launch a remote access trojan and a stealer that then establishes contact with a command-and-control (C2) server and exfiltrates browser-stored credentials, session tokens, and other sensitive data.
The loader, besides monitoring for analysis tools such as Wireshark, OllyDbg, Procmon, ProcExp, PeStudio, and Fiddler, makes Windows Registry changes to set up persistence and launches the second-stage by injecting it into a legitimate system process like “CasPol.exe” or “InstallUtil.exe” to evade detection.
The second-stage payload, obfuscated using .NET Reactor, is the PureHVNC RAT that contacts a remote server (185.149.232[.]197) and comes with capabilities to steal data from several cryptocurrency wallet extensions installed on Chromium-based browsers. PureHVNC also adopts a plugin-based approach to capture screenshots when window titles matching banks and wallets are opened.
Check Point said it identified no less than 70 promoted posts from fake social media pages impersonating Kling AI. It’s currently not clear who is behind the campaign, but evidence gathered from the fake website’s web page and some of the ads show that they could be from Vietnam.
The use of Facebook malvertising techniques to distribute stealer malware has been a tried-and-tested tactic of Vietnamese threat actors, who have been increasingly capitalizing on the popularity of generative AI tools to push malware.
Earlier this month, Morphisec revealed that a Vietnamese threat actor has been leveraging fake AI-powered tools as a lure to entice users into downloading an information stealer malware dubbed Noodlophile.
“This campaign, which impersonated Kling AI through fake ads and deceptive websites, demonstrates how threat actors are combining social engineering with advanced malware to gain access to users’ systems and personal data,” Check Point said.
“With tactics ranging from file masquerading to remote access and data theft, and signs pointing to Vietnamese threat groups, this operation fits into a broader trend of increasingly targeted and sophisticated social media-based attacks.”
The development comes as The Wall Street Journal reported that Meta is battling an “epidemic of scams,” with cyber criminals flooding Facebook and Instagram with various kinds of scams ranging from romance baiting to sketchy bargain ads to fake giveaways. Many of the scam pages are operated from China, Sri Lanka, Vietnam, and the Philippines, the report added.
According to Rest of World, phony job ads on Telegram, Facebook, and other social media are being increasingly used to lure young Indonesians and get trafficked to scam compounds in Southeast Asia, from where they are coerced into running investment scams and defraud victims across the world.
Found this article interesting? Follow us on Twitter and LinkedIn to read more exclusive content we post.