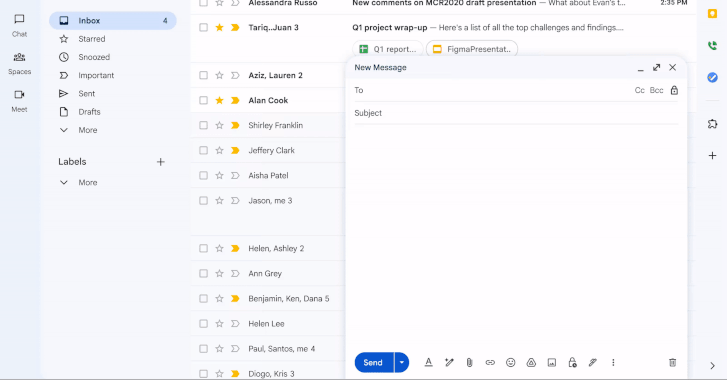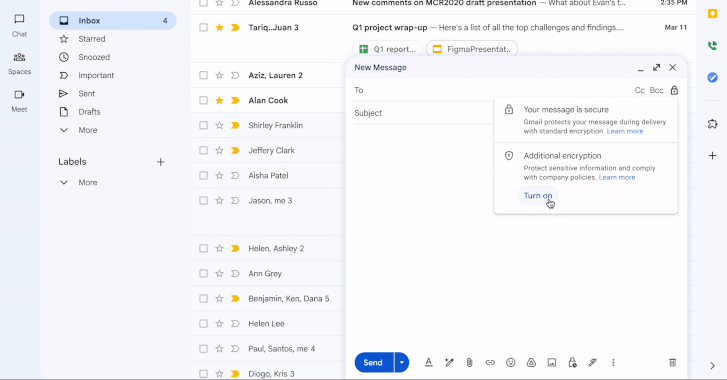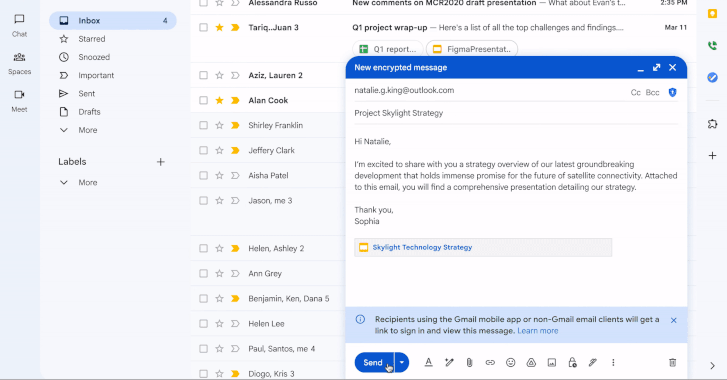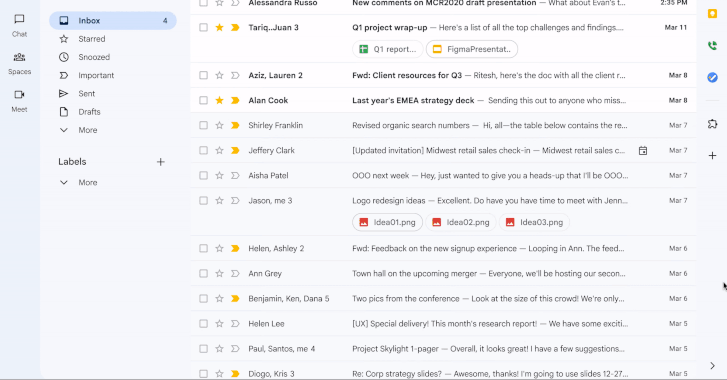
On the 21st birthday of Gmail, Google has announced a major update that allows enterprise users to send end-to-end encrypted (E2EE) to any user in any email inbox in a few clicks.
The feature is rolling out starting today in beta, allowing users to send E2EE emails to Gmail users within an organization, with plans to send E2EE emails to any Gmail inbox in the coming weeks and to any email inbox