ACM.100 Using an EIP to obtain a fixed IP address for EC2 instances and network interfaces
This is a continuation of my series of posts on Automating Cybersecurity Metrics.
In a prior post I had to switch my IP address to an IP address that was already allowed through my local firewall so I could connect to it.
Connecting to an EC2 instance via SSH (and when you can’t)
In this post I’m going to replace that existing IP address with an Elastic IP Address (EIP). By using an EIP I will have a fixed IP address that remains consistent when my EC2 instance (VM) on AWS is stopped and started. I can also point that IP address at different VMs.
I’m going to deploy the EIP with a CloudFormation template. Then I’m going to associate that new IP address to the Developer EC2 instance we deployed.
Automated Deployment of an EC2 Instance with the Latest AWS Linux AMI
Your company may have an AWS Direct Connect or a VPNs to create private connections to AWS. In some smaller companies, or if you are a single user connecting to your own cloud account, you might use the simple options I will present below to improve security for your cloud resources. You may also need a static IP in some cases such as for a penetration test or some other connection to a third-party with network restrictions, as I explain below.
Default AWS EC2 Instance IP Address
When you deploy EC2 instances on AWS with a public IP address you don’t control the IP address assigned to your instance by default. AWS controls that. You will get an address assigned from one of the many IP addresses in the AWS address space. As I wrote about before you can find those here:
https://ip-ranges.amazonaws.com/ip-ranges.json
One of the problems with these random assignments of IP addresses is that it makes it very difficult to construct firewall rules. You don’t know which IP address you need to allow, therefore you may end up simply allowing all of the AWS IP ranges. Then what happens?
Well in some cases attackers leverage AWS and other cloud providers to carry out their attacks because they know that’s what you’ve done. One example was the Solar Winds breach. I explained how attackers used Azure and AWS in this post:
SolarWinds Hack: Retrospective
Firewall rules often need an IP address or CIDR block. That depends on whether the firewall is stateless or stateful — terms I explain in my book at the bottom of this post and in prior posts on this blog. Stateless firewalls inspect individual packets which don’t have full application layer data like fully qualified domain names (FQDNS). A stateful firewall will put the packets back together to perform inspection and enforce rules. There are reasons why each are beneficial in your overall network architecture.
Even if you can use a domain name in your network rules, you will also still have problems with DNS when it comes to firewall rules and EC2 instances. Your domain name is configured to send someone to a particular IP address. Then you decide you need to stop and start your EC2 instance. Now it has a new IP address. Your DNS records no longer resolve to the correct host.
Someone else happens to start an EC2 instance and get your old address. Now your website visitors are getting some other machine. If that machine happens to server up a website your domain would be pointing to some other website!
I was extremely concerned about this issue when deploying a bastion host at Capital One. Developers were supposed to use a domain name to get to it to login — potentially with production credentials. The person operating the DNS servers couldn’t understand why a 1 hour TTL was too long.
Elastic IP Address
Instead of depending on domain names, we can use an elastic IP address (EIP) on AWS to give an EC2 instance or load balancer or some other resource a fixed IP address. You configure a fixed IP address from AWS and then you can assign it to various resources. You can also disassociate an IP address and assign it to a new IP address later.
It’s very flexible but you are limited to 5 per region for an IPv4 address.
Additionally be aware that you will not be charged for an EIP in use but if you do not have it assigned to any resource you will be billed for it. Click on Elastic IP Addresses on this page to see the pricing.
EC2 On-Demand Instance Pricing – Amazon Web Services
Another option is to bring your own IP to AWS. This topic is more complicated than we’re going to get into in this series but you can read about it here.
Bring your own IP addresses (BYOIP) in Amazon EC2
It also appears that you may be able to request contiguous fixed IP addresses.
How to reserve the consecutive EIP? | AWS re:Post
Why does that matter? Let’s say you have 5 IP addresses. If the addresses are continuous you can use a single entry with a CIDR block to allow access to your IP range. Otherwise you need a single rule in your network rules for each address. Now let’s say that you are using Active Directory have to open 50 separate ports and protocols (that’s what it felt like when I was trying to implement it anyway). 50 x 5 = 250 rules.
Let’s say you are in a complex networking environment that has acquired many companies and has numerous forests and trees for AD and none of them are contiguous. I’ve having flashbacks. You get the idea. That problem is part of the reason you can now add more rules for security groups on AWS than used to be possible. It was another one of our feature requests while I was at Capital One.
Luckily, AWS has come up with a new feature that can help with that issue called Prefix Lists. I’ll write more about those in a few posts. You can add a list of IPs to a prefix list and use that in Security Groups and Firewalls. It won’t work for AWS NACLs, however.
Work with customer-managed prefix lists
Uses for elastic IP addresses to improve security
Sometimes customers want me to provide a fixed IP address for a penetration test. I don’t prefer this approach because it’s too easy to miss something when only using a fixed IP that somehow gets blocked or processed differently than new IP Addresses, but if it is a requirement I can use a an EIP.
I started writing about my home network and how I am configuring and testing firewall products. Sorry I’m still not done with this I just have too many interests but hope to get back to it soon. I need the code in the series I’m writing for business projects so it comes first. Anyway, you can configure your home firewall to only allow SSH access to specific hosts if you assign an EIP. There are other ways, some better than others. I don’t like using DNS services that are not truly vetted, for example. A VPN would be another good option.
In addition, you can specify that only certain IP addresses are allowed access in certain cloud services like GitHub. If you use an EC2 instance to download and access code in a private GitHub account you can lock it down to only the IP addresses you want to authorize. I’ll show you that in a minute. I prefer to only use cloud services that let me control access via IP addresses in that way.
Creating an EIP in CloudFormation
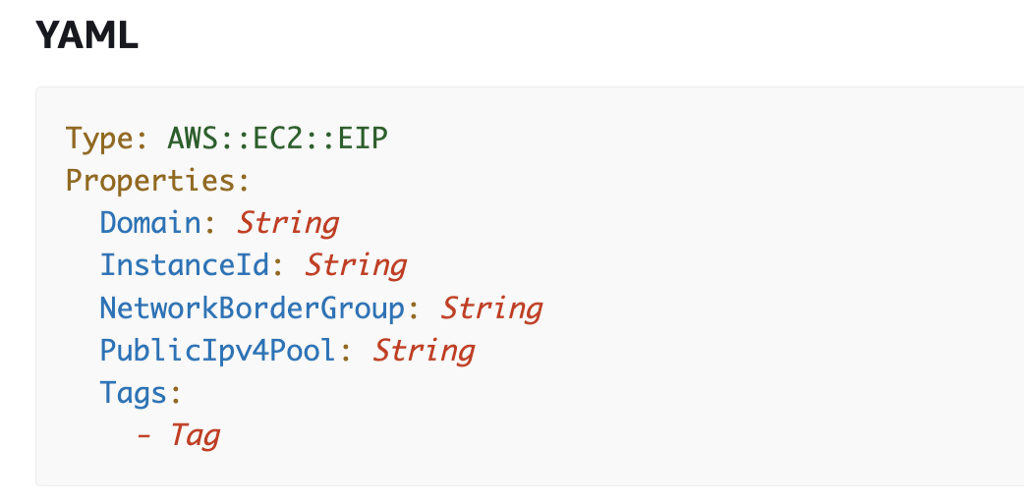
Here are the properties available to us when creating an EIP in CloudFormation.
The only properties that I am really concerned about are the following:
Tags — Tag: I want to use a tag to identify the IP address with a name.
InstanceId: we can associate the EIP with an EC2 instance.
The InstanceId is not required, so we can create the EIP and associated it at a later time using the EIP Association CloudFormation resource. This option might be necessary if an EC2 instance has multiple interfaces or you want to associate the IP with a network interface rather than an EC2 instance.
Separation of Duties for EIPs to prevent network misconfigurations
The EIP should probably be created under networking. Our network administrators will control the creation of IP addresses. We might also want them to control which resources can be assigned which IP addresses.
Let’s say that you have a rogue user who wants to access a production resource but he or she cannot. If that person can associate a resource they are not supposed to access due to networking rules with an EIP they are allowed to access through the firewall they might be able to access something they should not.
Refer to my prior blog post for an example where I couldn’t get through my firewall to AWS, so I disassociated an IP address from an existing instance and assigned it to the instance to which I wanted to connect. 😀 Mwa-ha-ha. Don’t let users in your cloud environment like me do such things if they are not supposed to be doing that. Also, by segregating permission to create EC2 instances from managing networking, a network administrator couldn’t do that either. They have permission to create the IP address, but not permission to run a new EC2 instance that can use it.
EIP CloudFormation Dependency considerations
Alright so network administrators will create and assign EIPs so we have some new dependency considerations. We need the networking before we can create the EC2 instance but the EC2 instance before we create the EIP. We’ll want to create a separate deploy script for the EIP so we can correctly order all the things in our test and delete script.
Simple EIP Template
Let’s start with a simple EIP template and see if it works. I put this in EIP.yaml in my Networking CloudFormation (cfn) directory.
Next I need to update the deploy script — but notice that we need to pass in two parameters. How am I going to get the instance ID? Recall that we had an output when we created our developer EC2 instance:
We can reference that in our deploy script. I’ll create a new deploy script called deploy_eip.sh for the reasons mentioned above. I’m going to need to change the instance ID to reference that export, so I’ll pass in the export name, and use the export with an ImportValue function to get the Instance ID in my template:
Next I added a function to network_functions.sh
By the way, I initially used the $name for my variable and got weird results. So need to move this out of bash but this is is the fastest way to get the initial POC done. Stay tuned for a better option (hopefully I will have time).
Now I can call the function from my deploy_eips.sh script.
And test it out…that worked. And our output for the EIP stack has the new IP address in case we need it. Note that this is NOT my IP in the screenshot below anymore so don’t be calling it up like 867–5309. If you’re old you know what I’m talking about. 🙂
You can also take a look at the list of EIPs on the EC2 dashboard and check your EC2 instance to verify that the the IP address was assigned correctly.
You will see that public IP address on your EC2 instance as well. Notice that even though my instance is stopped it still has the public IP assigned:
Now that may or may not be enough to allow you to connect to that host on AWS. It depends on your local network. In the next post, I’ll show you how to configure local network firewall rules.
Follow for updates.
Teri Radichel
If you liked this story please clap and follow:
Medium: Teri Radichel or Email List: Teri Radichel
Twitter: @teriradichel or @2ndSightLab
Requests services via LinkedIn: Teri Radichel or IANS Research
© 2nd Sight Lab 2022
All the posts in this series:
Automating Cybersecurity Metrics (ACM)
____________________________________________
Author:
Cybersecurity for Executives in the Age of Cloud on Amazon
Need Cloud Security Training? 2nd Sight Lab Cloud Security Training
Is your cloud secure? Hire 2nd Sight Lab for a penetration test or security assessment.
Have a Cybersecurity or Cloud Security Question? Ask Teri Radichel by scheduling a call with IANS Research.
Cybersecurity & Cloud Security Resources by Teri Radichel: Cybersecurity and Cloud security classes, articles, white papers, presentations, and podcasts
Deploying an AWS Elastic IP Address was originally published in Cloud Security on Medium, where people are continuing the conversation by highlighting and responding to this story.