As a relatively new security category, many security operators and executives I’ve met have asked us “What are these Automated Security Validation (ASV) tools?” We’ve covered that pretty extensively in the past, so today, instead of covering the “What is ASV?” I wanted to address the “Why ASV?” question. In this article, we’ll cover some common use cases and misconceptions of how people misuse

- November 21, 2024
- by
- Cyber News
- Less than a minute
- 101 Views
Related Post
- by Francis Schmuff
- June 8, 2025
New Supply Chain Malware Operation Hits npm and
Cybersecurity researchers have flagged a supply chain attack targeting over a dozen packages associated with GlueStack to deliver malware. The
- by Francis Schmuff
- June 8, 2025
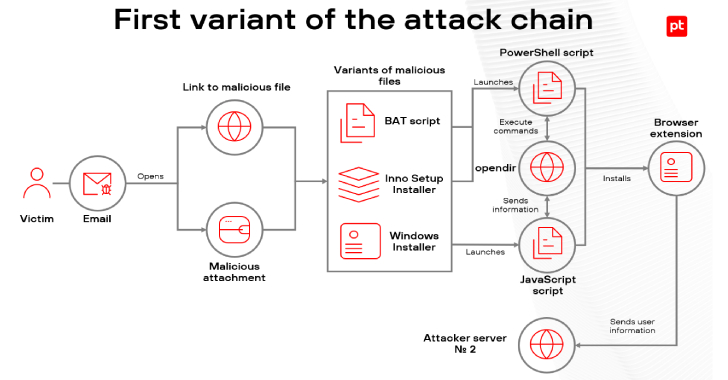
Malicious Browser Extensions Infect Over 700 Users Across
Cybersecurity researchers have shed light on a new campaign targeting Brazilian users since the start of 2025 to infect users
- by Francis Schmuff
- June 6, 2025
Friday Squid Blogging: Squid Run in Southern New
Southern New England is having the best squid run in years. As usual, you can also use this squid post
- by Francis Schmuff
- June 6, 2025
Hearing on the Federal Government and AI
On Thursday I testified before the House Committee on Oversight and Government Reform at a hearing titled “The Federal Government