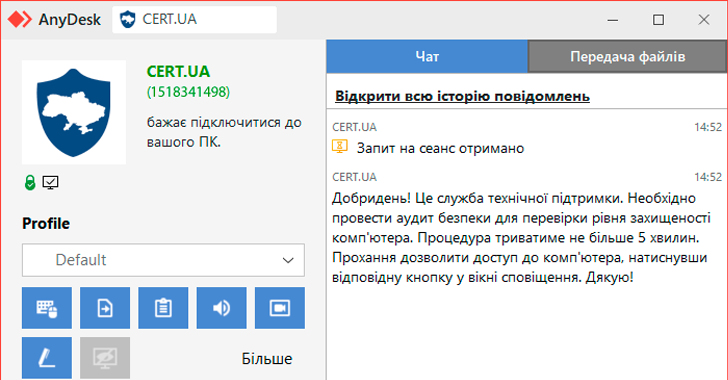
The Computer Emergency Response Team of Ukraine (CERT-UA) is warning of ongoing attempts by unknown threat actors to impersonate the cybersecurity agency by sending AnyDesk connection requests.
The AnyDesk requests claim to be for conducting an audit to assess the “level of security,” CERT-UA added, cautioning organizations to be on the lookout for such social engineering attempts that seek to