The Computer Emergency Response Team of Ukraine (CERT-UA) is warning of a new campaign that targets the defense sectors with Dark Crystal RAT (aka DCRat).
The campaign, detected earlier this month, has been found to target both employees of enterprises of the defense-industrial complex and individual representatives of the Defense Forces of Ukraine.
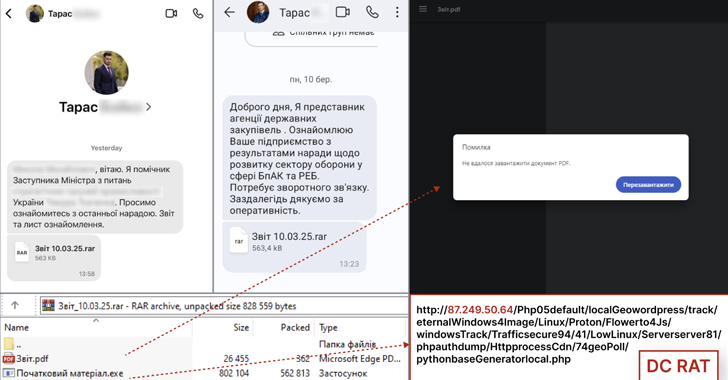
The activity involves distributing malicious messages via the Signal messaging app that contain supposed meeting minutes. Some of these messages are sent from previously compromised Signal accounts so as to increase the likelihood of success of the attacks.
The reports are shared in the form of archive files, which contain a decoy PDF and an executable, a .NET-based evasive crypter named DarkTortilla that decrypts and launches the DCRat malware.
DCRat, a well-documented remote access trojan (RAT), facilitates the execution of arbitrary commands, steals valuable information, and establishes remote control over infected devices.
CERT-UA has attributed the activity to a threat cluster it tracks as UAC-0200, which is known to be active since at least summer 2024.
“The use of popular messengers, both on mobile devices and on computers, significantly expands the attack surface, including due to the creation of uncontrolled (in the context of protection) information exchange channels,” the agency added.
The development follows Signal’s alleged decision to stop responding to requests from Ukrainian law enforcement regarding Russian cyber threats, according to The Record.
“With its inaction, Signal is helping Russians gather information, target our soldiers, and compromise government officials,” Serhii Demediuk, the deputy secretary of Ukraine’s National Security and Defense Council, said.
Signal CEO Meredith Whittaker, however, has refuted the claim, stating “we don’t officially work with any gov, Ukraine or otherwise, and we never stopped. We’re not sure where this came from or why.”
It also comes in the wake of reports from Microsoft and Google that Russian cyber actors are increasingly focusing on gaining unauthorized access to WhatsApp and Signal accounts by taking advantage of the device linking feature, as Ukrainians have turned to Signal as an alternative to Telegram.
Found this article interesting? Follow us on Twitter and LinkedIn to read more exclusive content we post.