ACM.88 Deploy and instance in the Developer VPC created Earlier and Test Remote Access
This is a continuation of my series of posts on Automating Cybersecurity Metrics.
We already spent a few posts considering ways to authenticate and log into an EC2 instance and for now, we will use an SSH key. You can follow along with how that key got created and stored in a Secrets Manager secret accessible to one user only starting here (there are multiple posts on the topic):
Automated Creation of an SSH Key for an AWS User
CloudFormation for an EC2 instance
I’m going to give you a script that we can use that I provided to students in class, with a few modifications.
Outputs referenced:
VPC, Subnet, and the SSH Security Group ids from from the corresponding stack outputs. We created this networking in the posts that started here:
Parameters:
Linux AMI ID: An Amazon Machine Image (AMI) is a VM configuration that you can use to create new VMs. It includes the Operating System, install software, data, and settings.
Username: A username to tag the instance and stack.
Key Name: We are going to create an SSH key for this user and the key name will also be the username. The key name will be reference in the CloudFormation template.
Code: This could be anything like a team, department, or project. It is added to the name of the instance. For example, if every AMI related to a particular project started with the same code or prefix it would be easy to query those instances by name in the AWS console. I’m going to use the code ACM (Automating Cybersecurity Metrics or the name of this blog series).
Instance Type: The AWS instance type which is t4g.small by default but can be overridden.
Note that we are not adding encryption to this AMI here yet — an AWS best practice. Follow along to the next post for that.
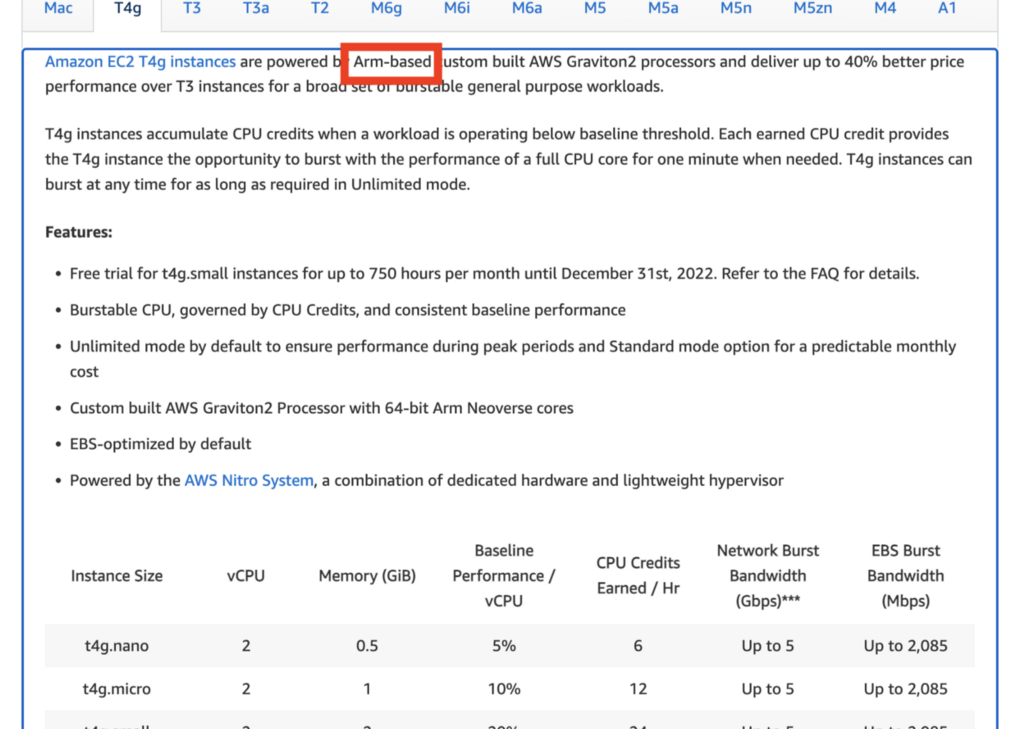
About Instance Types and Sizes
Note that at the time of this writing the default instance size used by the template (which you can override) is a T4g small instance.
You can review the different types of virtual machines available on AWS here. As you may recall, for Linux you can choose from Arm or x86. Arm may be cheaper but sometimes when you’re trying to run software that is compiled for x86 you’re going to have challenges. You’ll need to recompile the software or switch to x86.
You can check information in the description that describes the processor to determine if it is arm or x86, but AWS could make this a bit clearer by just spelling our arm or x86 in a consistent way.
Amazon EC2 Instance Types – Amazon Web Services
Permissions for the AppDeploy Role
For this framework I’m going to have the AppDeploy role deploy EC2 instances. You can name these roles whatever you want if you don’t like my names, but I’m using AppDeploy to deploy compute resources in the account. Through trial and error I figured out I need these permissions to run our template. Note that we are not going to allow this user to assign a role to an EC2 instance just yet. We don’t even have any roles that can be used with EC2 instances at this time.
VM Functions
I created two functions in my VM functions script.
get_lastest_ami: This function gets the latest AMI. In order to get the latest AMI we need the architecture for the type of AMI we want to retrieve. In my case I default to arm64 if not architecture is set. This will be for Linux type instances and will pull the latest arm64 AMI (until AWS changes their naming conventions).
deploy_vm: In this function, we get the necessary parameters and call the deploy_stack function.
Deploy Script
The deploy script is pretty simple. Get the latest AMI using our get_latest_ami function. Then call deploy_vm with the appropriate parameters.
CloudFormation Template
We’re starting to get a lot of resources in our account. This is where our naming convention comes in handy. We can search on Network-VPC to find the VPCs we created. We want to use the Developer VPC. Click on that stack.
We’re going to get the VPC ID from the outputs as we have been doing all along with our common function in this series.
Using those outputs our template to deploy an EC2 instance ends up looking like this:
For now I’m just naming the instance with the name of the user “Developer” and the AMI ID, the instance type, and AMI ID.
For the outputs I had to leave out InstanceType since it has invalid characters.
If we go check out the EC2 dashboard you can see I had a few failed attempt to deploy my EC2 instance while trying to determine the necessary permissions, but once I figured those out I got my instance running with the correct name.
Next Steps…
In your own organization you will likely create your own AMI that is aligned with your security standards. Out of the gate, AWS EC2 instances are not CIS Benchmarks compliant. If you want to use an EC2 instance that is you can find some in the AWS Marketplace. Make sure you get them from the correct source (The Center for Internet Security) because back in the day I remember that bad actors would try to create images that looked like they were coming from Amazon but they were not.
You can even modify the query above to get the latest CIS benchmarks AMI but I’m not going to do that here — I’ll leave that as an exercise for the reader. 🙂
In addition we want to encrypt our AMI with our own developer KMS key. That way only our developers that have permission to use that key can access our EC2 instance.
Follow for updates.
Teri Radichel
If you liked this story please clap and follow:
Medium: Teri Radichel or Email List: Teri Radichel
Twitter: @teriradichel or @2ndSightLab
Requests services via LinkedIn: Teri Radichel or IANS Research
© 2nd Sight Lab 2022
All the posts in this series:
Automating Cybersecurity Metrics (ACM)
____________________________________________
Author:
Cybersecurity for Executives in the Age of Cloud on Amazon
Need Cloud Security Training? 2nd Sight Lab Cloud Security Training
Is your cloud secure? Hire 2nd Sight Lab for a penetration test or security assessment.
Have a Cybersecurity or Cloud Security Question? Ask Teri Radichel by scheduling a call with IANS Research.
Cybersecurity & Cloud Security Resources by Teri Radichel: Cybersecurity and Cloud security classes, articles, white papers, presentations, and podcasts
Automated Deployment of an EC2 Instance with the Latest AWS Linux AMI was originally published in Cloud Security on Medium, where people are continuing the conversation by highlighting and responding to this story.