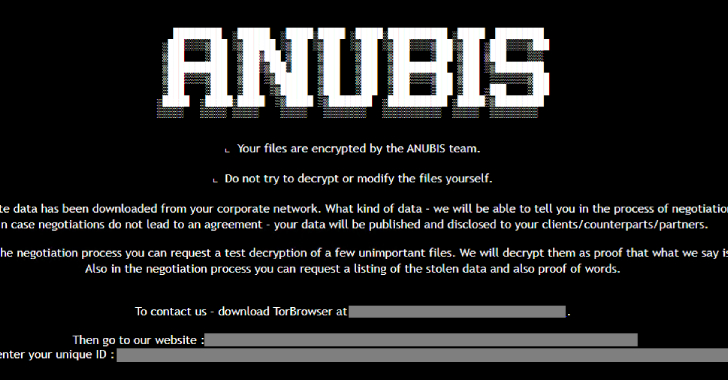
An emerging ransomware strain has been discovered incorporating capabilities to encrypt files as well as permanently erase them, a development that has been described as a “rare dual-threat.”
“The ransomware features a ‘wipe mode,’ which permanently erases files, rendering recovery impossible even if the ransom is paid,” Trend Micro researchers Maristel Policarpio, Sarah Pearl Camiling, and