ACM.140 Trying to figure out conditions and ARNs to create a delegated administrator for SCPs
This is a continuation of my series on Automating Cybersecurity Metrics.
In my last post I wrote about how I wanted to create a delegated admin account for SCPs. I also noted that the documentation, at the time of this writing, is a bit unclear as to if this will even work, and it doesn’t provide all the necessary information to set it up.
Delegated Administrator for AWS Organizations
I’m sure that will be updated at some point, but in the meantime let’s see if we can figure out what’s in a request in CloudTrail when you create an SCP. I’m going to create an SCP in my root AWS Organizations account and take a look.
You may recall that this all started when I was trying to protect my domain names. We can start with a global administration policy to restrict domain actions.
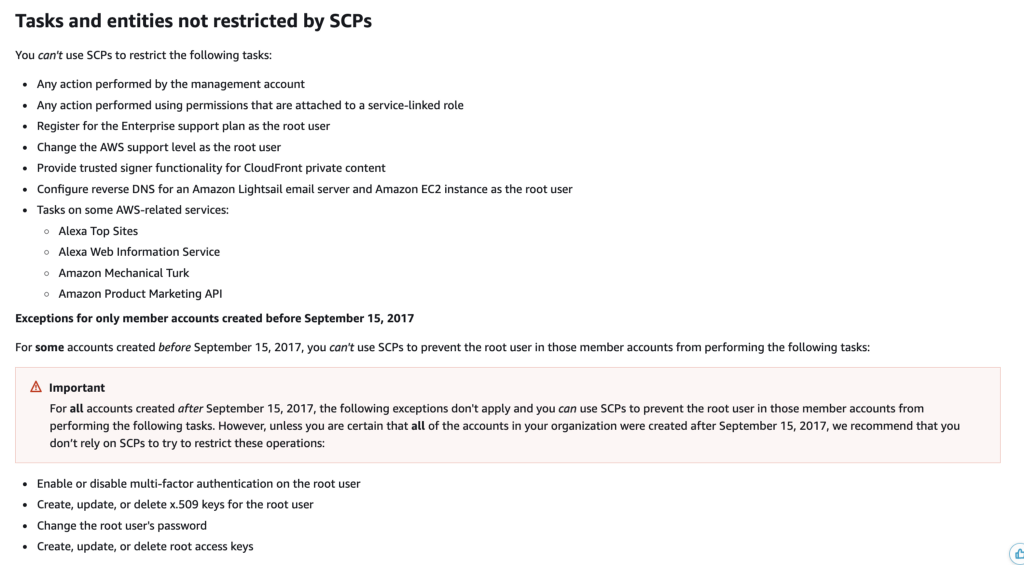
The documentation says that SCPs do not apply to the root management account, so any SCP we create won’t lock us out of our own resources, if true. The root management account should still have access, and can revert the SCP if needed. There are a number of other scenarios where SCPs do not apply listed here.
Service control policies (SCPs)
I had to revise my earlier blog post on Letting Governance Teams Govern after reading the documentation again. AWS Service-Linked roles are unaffected, and after reconsidering, it is not clear if the roles created by AWS Organizations and AWS Control Tower would fall into that category. Something to keep in mind and I’ll be exploring further later.
Letting Governance Teams Govern
Sample Service Control Policies (SCPs)
AWS provides some Sample SCPs you can take a look at to get an idea what you can do with an SCP and how to write one. As I’ve said many times before, do not blindly copy and paste code off the web — even from a cloud vendor. Analyze it and test it to make sure it does what you want, and only what you want, securely.
Example service control policies
Also note that some of these policies may already be in place if you are using AWS Control Tower or someone has created them in your account. To view Service Control Policies you can navigate to AWS Organizations, then Policies.
Click on Service Control Policies.
You can take a look at the policies to see what’s in them by clicking on any policy.
In this policy only the Control Tower Execution role is allowed to perform certain actions:
The role in the policy above is one of the roles I mentioned that may not be affected by our Service Control Policies. It would be nice if AWS could somehow provide a list of roles that will not be affected, just to be very explicit about the problem. Then customers could check to see how those roles are used in their accounts and what permissions they have.
Creating a Service Control Policy Manually
There’s the perfect way to do things and the get things done way. Ideally I want to automate creation of Service Control Policies. But to get immediate protection of my domain names across my organization, with the exceptions for roles not impacted as noted above, I’m going to manually create a Service Control Policy.
Click Create on the page listing all your service control policies.
Now, I could try to be super smart and only allow one particular role to manage my domains, but for right now, I just want to completely block that throughout my organization. I can always come back in and add the permission later.
In my case, there is little risk because I am the only one working in my account. In your case, you may be working in a large organization and I don’t recommend this approach! Who knows what functionality might break. Test first in a separate branch of your organization.
Mainly I just want to create an SCP and see the request in CloudTrail.
Enter a name. The input box nicely tells you the formats allowed. You might want to think about a naming convention here. Perhaps your convention is by service, or you have different SCPs for different lines of business. Since this SCP is applicable to my entire organization I’ll name it as such. We’ll see how this naming convention works out.
Here’s my policy:
At this point I get an error so I recreate my policy:
Inconsistent naming policies strikes again. Cannot have dashes in an IAM Policy Statement Sid.
I can see that my policy has been added. I can also see that the Control Tower policy descriptions are not very descriptive. They are all the same.
What does a request look like in CloudTrail?
Navigate to CloudTrail and try to find our actions. I tried to look up actions on the resource “ServiceControlPolicy” but it doesn’t exist in the list:
I just return to the default settings, clear true/false and hit enter to see all events. Well these create data key events with no user or resource are interesting.
Something to do with CloudTrail but would be nice if AWS would populate all the data.
I try searching by my user name. It says I performed a bunch of actions I don’t recall doing like accessing an S3 bucket and looking at DescribeConfigurationRecorderStatus which I guess is related to opening the CloudTrail page? Not sure how I triggered that. I don’t see anything related to my Service Control Policy change.
When I look up events by event source (organizations) I don’t see that here either:
Do you know what the problem is? Age-old problem that still got me for a minute. The events are logged in a different region. Even though I set up AWS Control Tower in one region and I was in that region, AWS organizations is a global service:
The events related to creating SCPs will be in us-east-1 as a result. I need to switch to that region and return to CloudTrail to see those events.
Ok now I can see my actions in CloudTrail where I created policies. I basically guessed this in my last post but it’s nice to know for certain. The policy type we need to use for our delegated administrator account policy is SERVICE_CONTROL_POLICY. Makes perfect sense!
There was one other thing I needed — an ARN. Perhaps. The last line of this portion of the sample delegated administrator policy refers to resources with backup_policy in the ARN.
We can get that ARN from our policy, actually. Take a look at any of your SCPs and they will have a similar ARN. The variables we want to abstract or extract if you prefer that will change from organization to organization are shown below. I want to have a way to deploy this that will work for any organization.
What is interesting in the example above, is that the backup_policy ARN in the example is structured differently. It does not include the organization ID. Perhaps backup policy ARNs are structured differently.
Well, it seems that we have what we need now to create our delegated administrator policy. I’ll try that out in the next post — probably. 🙂 Unless I start doing that and hit another speed bump along the way.
Follow for updates.
Teri Radichel
If you liked this story ~ clap, follow, tip, buy me a coffee, or hire me.
Medium: Teri Radichel
Email List: Teri Radichel
Twitter: @teriradichel
Twitter (company): @2ndSightLab
Mastodon: @teriradichel@infosec.exchange
Post: @teriradichel
Facebook: 2nd Sight Lab
Slideshare: Presentations by Teri Radichel
Speakerdeck: Presentations by Teri Radichel
Books: Teri Radichel on Amazon
Recognition: SANS Difference Makers Award, AWS Hero, IANS Faculty
Certifications: SANS
Education: BA Business, Master of Sofware Engineering, Master of Infosec
How I got into security: Woman in tech
Buy me a coffee: Teri Radichel
Company (Penetration Tests, Assessments, Training): 2nd Sight Lab
Request services via LinkedIn: Teri Radichel or IANS Research
Request services via LinkedIn: Teri Radichel or IANS Research
© 2nd Sight Lab 2023
All the posts in this series:
Automating Cybersecurity Metrics (ACM)GitHub – tradichel/SecurityMetricsAutomation
____________________________________________
Author:
Cybersecurity for Executives in the Age of Cloud on Amazon
Need Cloud Security Training? 2nd Sight Lab Cloud Security Training
Is your cloud secure? Hire 2nd Sight Lab for a penetration test or security assessment.
Have a Cybersecurity or Cloud Security Question? Ask Teri Radichel by scheduling a call with IANS Research.
Cybersecurity & Cloud Security Resources by Teri Radichel: Cybersecurity and Cloud security classes, articles, white papers, presentations, and podcasts
Analyzing CloudFormation Requests Related to SCPs was originally published in Cloud Security on Medium, where people are continuing the conversation by highlighting and responding to this story.