ACM.120 Add more than once MFA device to an IAM account for different purposes or in case of a lost device
This is a continuation of my series on Automating Cybersecurity Metrics.
I’m thrilled to see that we can now add multiple MFA devices to a user in AWS IAM. I’m stopping in the middle of another blog post to try it out. AWS SSO already allows multiple keys but there are a few things you can’t do with AWS SSO and may still want to use AWS IAM in some cases as explained in this blog series.
Why you might want multiple MFA keys for your AWS IAM account
I spoke about why this feature is needed at the AWS Atlanta Summit earlier this year. Let’s say you use a Yubikey and you have a crazy dog like the one we just got it might be running around by your computer and break your Yubikey. You can use a backup device to access your account.
In fact, earlier this year my husband was goofing around when I was working on my computer and I almost completely destroyed a Yubikey. Luckily it had two ends and the one that worked in my mobile phone still worked so I could still get into some of my accounts that used that key.
There’s also the possibility that you could lose your key or it simply stops working. What about your root account? Perhaps you have two different keys stored in two separate places in case one or other locations is affected by a disaster.
Separate MFA devices for automation and the AWS Console
I explained why I don’t use Yubikeys with the AWS CLI here:
Although I don’t want to install the Yubikey CLI if I don’t have to on my primary work machine, I do like using a Yubikey best to login to websites.
It would be great if I could use a Yubikey for the AWS Console (web site) but a virtual MFA device for automation. That’s what I’m going to try out.
Adding a Yubikey to our IAM User account
We used CloudFormation to deploy a user account.
Create an IAM User with CloudFormation
I explained how to use MFA with the AWS CLI in this post with virtual MFA:
Using an AWS CLI Profile with MFA
In this post we used CloudFormation to auto-generate a password to use with the AWS console.
Autogenerated Passwords in CloudFormation for AWS Console Access
We leverage the AWS Console to enforce access to a user-specific AWS Secrets Manager Secret using MFA. Because I could only add one MFA device to our user I have been using the virtual MFA device to log into the console and with automation.
User-Specific Secrets: Console Access
Now I want to know if I can use a separate device for the AWS Console and automation.
Adding a second MFA device in the AWS Console
Login to the AWS Console.
Click on the user for whom you want to add the second MFA device.
Note that the first time I logged in and looked at the screen where you
can edit MFA, I initially did not see the new screen. I could only add
one device. I added a new user and there I could see the new screen.
Then I looked at a different user that had MFA assigned and there was no
MFA device assigned! What? Not to worry. Clicking around some more, I
was able to see the new MFA screen and all the existing MFA devices
were present. It could be that AWS was rolling out updates or a caching
issue but just click around a bit and you should be able to see the screen
below if you don’t at first for an existing user.
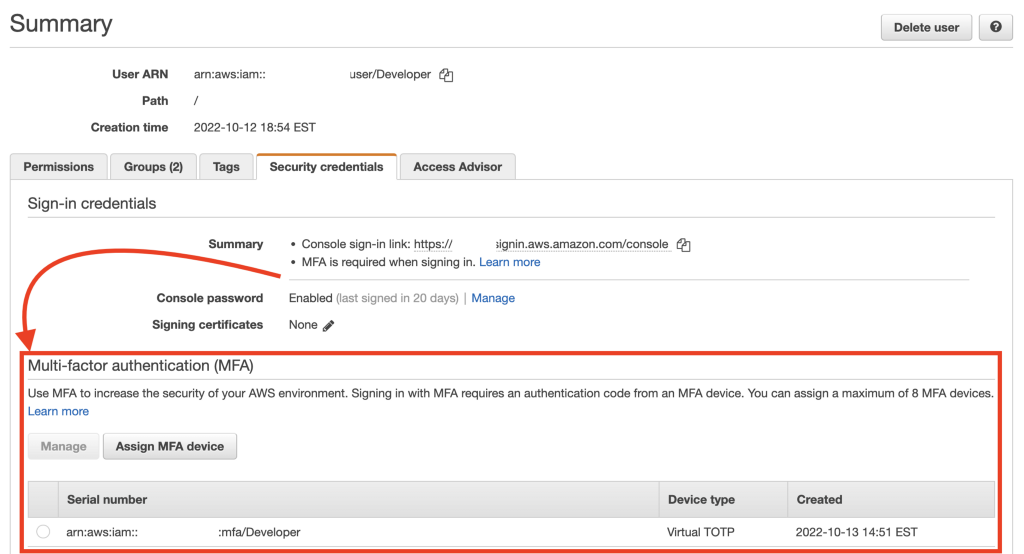
MFA devices have moved to a list under the user password section.
We already have a virtual MFA device assigned.
Let’s see if we can add a hardware device also. Click “Assign MFA Device.”
Enter a Name. Select Security key.
After entering the pin for my device and clicking the buttom I now have two different types of MFA devices associated with the developer account.
If you recall from the post on using MFA with the CLI you specify a particular MFA device to use with a profile. For our Developer user, we can specify the virtual MFA device as our MFA device for automation.
Now you can test logging into the AWS Console using your new hardware MFA device assigned to the Developer IAM user.
One thing I would like to explore further: the ability to limit automation to a specific MFA device and console access to another.
Follow for updates.
Teri Radichel
If you liked this story please clap and follow:
******************************************************************
Medium: Teri Radichel or Email List: Teri Radichel
Twitter: @teriradichel or @2ndSightLab
Requests services via LinkedIn: Teri Radichel or IANS Research
******************************************************************
© 2nd Sight Lab 2022
All the posts in this series:
Automating Cybersecurity Metrics (ACM)GitHub – tradichel/SecurityMetricsAutomation
____________________________________________
Author:
Cybersecurity for Executives in the Age of Cloud on Amazon
Need Cloud Security Training? 2nd Sight Lab Cloud Security Training
Is your cloud secure? Hire 2nd Sight Lab for a penetration test or security assessment.
Have a Cybersecurity or Cloud Security Question? Ask Teri Radichel by scheduling a call with IANS Research.
Cybersecurity & Cloud Security Resources by Teri Radichel: Cybersecurity and Cloud security classes, articles, white papers, presentations, and podcasts
Multiple MFA Devices for IAM was originally published in Cloud Security on Medium, where people are continuing the conversation by highlighting and responding to this story.