Threat hunting is the process of looking for malicious activity and its artifacts in a computer system or network. Threat hunting is carried out intermittently in an environment regardless of whether or not threats have been discovered by automated security solutions. Some threat actors may stay dormant in an organization’s infrastructure, extending their access while waiting for the right

- November 18, 2022
- by
- Cyber News, Cyber Threat Trends
- Less than a minute
- 376 Views
Related Post
- by Francis Schmuff
- June 17, 2025
Meta Starts Showing Ads on WhatsApp After 6-Year
Meta Platforms on Monday announced that it’s bringing advertising to WhatsApp, but emphasized that the ads are “built with privacy
- by Francis Schmuff
- June 16, 2025
U.S. Seizes $7.74M in Crypto Tied to North
The U.S. Department of Justice (DoJ) said it has filed a civil forfeiture complaint in federal court that targets over
- by Francis Schmuff
- June 16, 2025
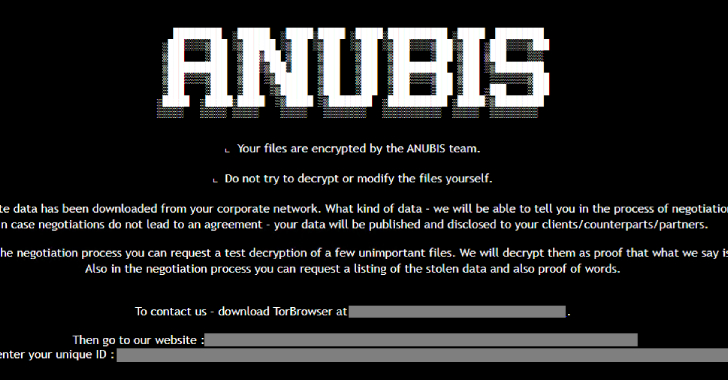
Anubis Ransomware Encrypts and Wipes Files, Making Recovery
An emerging ransomware strain has been discovered incorporating capabilities to encrypt files as well as permanently erase them, a development
- by Francis Schmuff
- June 16, 2025
⚡ Weekly Recap: iPhone Spyware, Microsoft 0-Day, TokenBreak
Some of the biggest security problems start quietly. No alerts. No warnings. Just small actions that seem normal but aren’t.