ACM.102 Ensuring only authorized IP addresses can access your private GitHub repositories
This is a continuation of my series on Automating Cybersecurity Metrics.
My last post explained how you can restrict SSH access on your local network to only authorized IP addresses.
Local Firewall Rules to Connect to an AWS EIP via SSH
Specifically, we allowed access to an EC2 instance we created in a network we deployed on AWS with CloudFormation. The networking on AWS restricts access to a specified IP address of one user connecting to an EC2 instance via SSH or RDP at the time of this writing. I might change that later. You can read everything leading up to this point here.
Automating Cybersecurity Metrics (ACM)
Now we want to protect our GitHub account and only allow specific IP addresses to access it. I’m going to show you how to do this, but keep in mind, that there’s no way to prevent the user in your AWS account to get to any other Github resource either. This is an OK solution for a single user or small company but larger organizations probably want to use a different configuration for deployment pipelines, as I discuss with customers on IANS Research consulting calls.
Protecting CloudResources with GitHub IP Allow Lists
You can add network restrictions to your GitHub account to help protect the resources in it. I am not going to tell you that it is the only thing you need to do to protect your GitHub account because there are ways around network restrictions in certain instances but they it will protect you from an attacker using your stolen credentials to get into your account — unless they have access to your network as well.
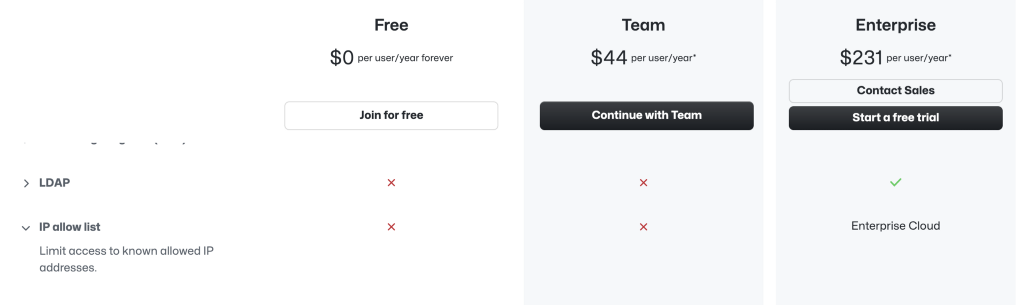
Managing allowed IP addresses for your organization – GitHub Enterprise Cloud Docs
You will need an Enterprise account.
Pricing · Plans for every developer
GitHub is not the only developer tool or cloud product that has these type of restrictions. You can do the same with GitLab:
I recommend that if your developer tools do not allow this, perhaps look elsewhere because it is such an important protection. Why network security is important was covered in these blog post and others.
Why You Need a VPCLambda Networking
Adding an IP restriction in GitHub
Let’s head over to GitHub and grant the IP access our GitHub repositories.
Alright a brief hiatus to say that I find the GitHub UI a bit convoluted and confusing when trying to switch around from a user to an organization and finding all the right settings. I wish they would figure out a way to make this more user-friendly and obvious. It’s not super difficult but I often find myself hunting around for things more than I do with other products and I’ve used GitHub for ages.
Click on your name on the top left and you should see your name, followed by your organization. Click on your organization.
Click View Organization on the left.
Click Settings (last on right)
Click on Authentication security (which doesn’t really make sense to me)
Note this error message at the top:
That warning is unclear. Does this mean you can no longer use IPv4 addresses? Or does it mean that you can use IPv6 addresses? Because if you can optionally use IPv6 then your IPv4 addresses should still work and there will be no “access interruptions.” The host and server should fall back to IPv4 where it is available if properly implemented. I hope this this documentation will be updated accordingly, and also provide the anticipated rollout date as well so people can properly prepare for this change.I mentioned earlier that I will not use IPv6 until forced to do. I mentioned that attackers are leveraging IPv6 misconfigurations and specifically when they can’t find any other way in. However, if GitHub forced use of only IPv6 here, then that would be the case to turn off IPv4 and start using IPv6. Right now it’s not clear that IPv4 is not available and they better not lock people out of using IPv4 without better messaging than the above. The message needs to be much more explicit if that’s what they are actually going to do. Something to keep an eye on.
Also, I wish the management UI was organized the way this documentation is because it’s very nice and makes sense to me:
Back to the GitHub UI, scroll down to IP Allow List. As the documentation states you’ll need to enable it first of all with the checkbox at the top.
Next add an IP with the add button at the bottom:
At the moment there seems to be a bug because when I click add I get this error message and I haven’t added an IP address yet. But anyway enter your IP address and a description if you like.
If you are only entering one IP address you don’t have to add /32 at the end like we did on AWS. It seems that a single IP or a CIDR will work here.
One warning: Make sure that you have multiple IPs set up in case you lose access to one, otherwise you wont’ be able to access your account.
Save it and that’s it. Now you should be able to access your GitHub repositories from your EC2 instance on AWS that you have given access — but no other instances on AWS or elsewhere with different IP addresses would be allowed.
Using your own GitHub server for greater control
Just a note that I often recommend that if customers have the option they may want to use their own hosted GitHub server if they want more control over the security and networking. Microsoft does own GitHub after all and if you are trying to protect the IP in your software repositories that may be a concern.
The other problem is that you might have is that you want people to use your corporate VPN to add additional encryption to traffic heading over to GitHub. There’s no way to configure a VPN on GitHub. Though you can configure access to resources behind a VPN from GitHub you can’t set up an IPSec Tunnel between your location and GitHub. As mentioned in prior posts and IPSec Tunnel will encrypt more layers of a packet than an SSL VPN or connection.
But since I am one person, this will have to do. I’m not overjoyed with the thought of managing a GitHub server. Hopefully GitHub is doing everything on their side correctly to secure this code, including preventing insider access to your code.
In the next post we’ll try to access to GitHub via our new firewall rules and restrictions.
Teri Radichel
If you liked this story please clap and follow:
Medium: Teri Radichel or Email List: Teri Radichel
Twitter: @teriradichel or @2ndSightLab
Requests services via LinkedIn: Teri Radichel or IANS Research
© 2nd Sight Lab 2022
All the posts in this series:
Automating Cybersecurity Metrics (ACM)
____________________________________________
Author:
Cybersecurity for Executives in the Age of Cloud on Amazon
Need Cloud Security Training? 2nd Sight Lab Cloud Security Training
Is your cloud secure? Hire 2nd Sight Lab for a penetration test or security assessment.
Have a Cybersecurity or Cloud Security Question? Ask Teri Radichel by scheduling a call with IANS Research.
Cybersecurity & Cloud Security Resources by Teri Radichel: Cybersecurity and Cloud security classes, articles, white papers, presentations, and podcasts
Limiting Access to an AWS EIP in GitHub was originally published in Cloud Security on Medium, where people are continuing the conversation by highlighting and responding to this story.