Several malicious Android apps that turn mobile devices running the operating system into residential proxies (RESIPs) for other threat actors have been observed on the Google Play Store.
The findings come from HUMAN’s Satori Threat Intelligence team, which said the cluster of VPN apps came fitted with a Golang library that transformed the user’s device into a proxy node without their knowledge.
The operation has been codenamed PROXYLIB by the company. The 29 apps in question have since been removed by Google.
Residential proxies are a network of proxy servers sourced from real IP addresses provided by internet service providers (ISPs), helping users hide their actual IP addresses by routing their internet traffic through an intermediary server.
The anonymity benefits aside, they are ripe for abuse by threat actors to not only obfuscate their origins, but also to conduct a wide range of attacks.
“When a threat actor uses a residential proxy, the traffic from these attacks appears to be coming from different residential IP addresses instead of an IP of a data center or other parts of a threat actor’s infrastructure,” security researchers said. “Many threat actors purchase access to these networks to facilitate their operations.”
Some of these networks can be created by malware operators tricking unsuspecting users into installing bogus apps that essentially corral the devices into a botnet that’s then monetized for profit by selling the access to other customers.
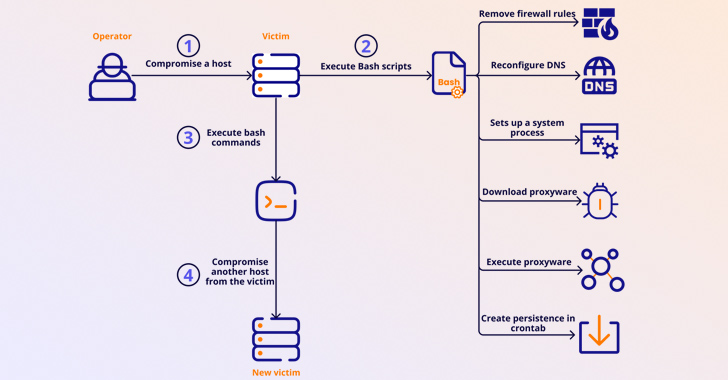
The Android VPN apps discovered by HUMAN are designed to establish contact with a remote server, enroll the infected device to the network, and process any request from the proxy network.
Another notable aspect of these apps is that a subset of them identified between May and October 2023 incorporate a software development kit (SDK) from LumiApps, which contains the proxyware functionality. In both cases, the malicious capability is pulled off using a native Golang library.
LumiApps also offers a service that essentially permits users to upload any APK file of their choice, including legitimate applications, and bundle the SDK to it without having to create a user account, which can then be re-downloaded and shared with others.
“LumiApps helps companies gather information that is publicly available on the internet,” the Israeli company says on its website. “It uses the user’s IP address to load several web pages in the background from well-known websites.”
“This is done in a way that never interrupts the user and fully complies with GDPR/CCPA. The web pages are then sent to companies, who use them to improve their databases, offering better products, services, and pricing.”
These modified apps – called mods – are then distributed in and out of the Google Play Store. LumiApps promotes itself and the SDK as an alternative app monetization method to rendering ads.
There is evidence indicating that the threat actor behind PROXYLIB is selling access to the proxy network created by the infected devices through LumiApps and Asocks, a company that advertises itself as a seller of residential proxies.
What’s more, in an effort to bake the SDK into as many apps as possible and expand the size of the botnet, LumiApps offers cash rewards to developers based on the amount of traffic that gets routed through user devices that have installed their apps. The SDK service is also advertised on social media and black hat forums.
Recent research published by Orange Cyberdefense and Sekoia characterized residential proxies as part of a “fragmented yet interconnected ecosystem,” in which proxyware services are advertised in various ways ranging from voluntary contributions to dedicated shops and reselling channels.
“[In the case of SDKs], the proxyware is often embedded in a product or service,” the companies noted. Users may not notice that proxyware will be installed when accepting the terms of use of the main application it is embedded with. This lack of transparency leads to users sharing their Internet connection without a clear understanding.”
The development comes as the Lumen Black Lotus Labs disclosed that end-of-life (EoL) small home/small office (SOHO) routers and IoT devices are being compromised by a botnet known as TheMoon to power a criminal proxy service called Faceless.
Found this article interesting? Follow us on Twitter and LinkedIn to read more exclusive content we post.