ACM.380 Accessing a private ECR repository and using the container to deploy resources in the remote account
- November 14, 2023
- by
- Cyber News, Cyber Threat Trends
- Less than a minute
- 381 Views
Related Post
- by Francis Schmuff
- August 7, 2025
Malicious Go, npm Packages Deliver Cross-Platform Malware, Trigger
Cybersecurity researchers have discovered a set of 11 malicious Go packages that are designed to download additional payloads from remote
- by Francis Schmuff
- August 7, 2025
Microsoft Discloses Exchange Server Flaw Enabling Silent Cloud
Microsoft has released an advisory for a high-severity security flaw affecting on-premise versions of Exchange Server that could allow an
- by Francis Schmuff
- August 7, 2025
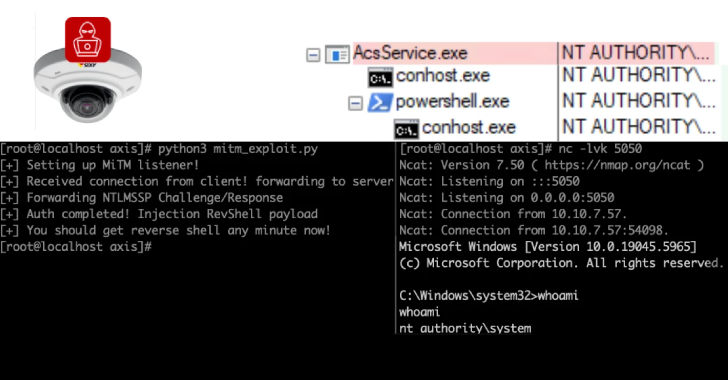
6,500 Axis Servers Expose Remoting Protocol, 4,000 in
Cybersecurity researchers have disclosed multiple security flaws in video surveillance products from Axis Communications that, if successfully exploited, could expose
- by Francis Schmuff
- August 7, 2025
The AI-Powered Security Shift: What 2025 Is Teaching
Now that we are well into 2025, cloud attacks are evolving faster than ever and artificial intelligence (AI) is both