Nearly 200 models are affected by vulnerability that may give wireless access to unauthorized third parties.

- August 1, 2023
- by
- Cyber News, Cyber Threat Trends
- Less than a minute
- 187 Views
Related Post
- by Francis Schmuff
- June 16, 2025
U.S. Seizes $7.74M in Crypto Tied to North
The U.S. Department of Justice (DoJ) said it has filed a civil forfeiture complaint in federal court that targets over
- by Francis Schmuff
- June 16, 2025
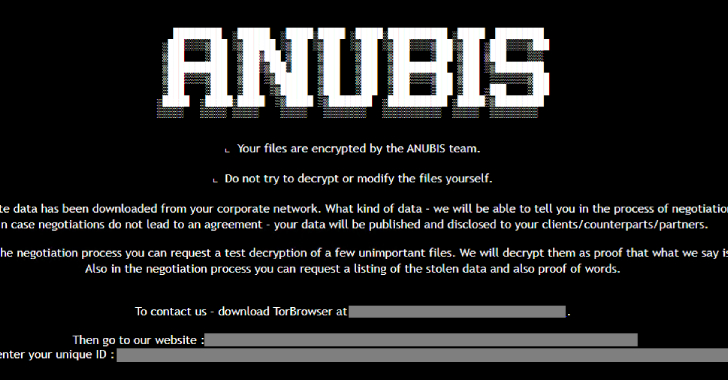
Anubis Ransomware Encrypts and Wipes Files, Making Recovery
An emerging ransomware strain has been discovered incorporating capabilities to encrypt files as well as permanently erase them, a development
- by Francis Schmuff
- June 16, 2025
⚡ Weekly Recap: iPhone Spyware, Microsoft 0-Day, TokenBreak
Some of the biggest security problems start quietly. No alerts. No warnings. Just small actions that seem normal but aren’t.
- by Francis Schmuff
- June 16, 2025
Playbook: Transforming Your Cybersecurity Practice Into An MRR
Introduction The cybersecurity landscape is evolving rapidly, and so are the cyber needs of organizations worldwide. While businesses face mounting