Accidentally typing a password in the username field of the platform saves them to audit logs, to which threat actors can gain access and use to compromise enterprise services.

- March 23, 2023
- by
- Cyber News, Cyber Threat Trends
- Less than a minute
- 202 Views
Related Post
- by Francis Schmuff
- April 3, 2025
Microsoft Warns of Tax-Themed Email Attacks Using PDFs
Microsoft is warning of several phishing campaigns that are leveraging tax-related themes to deploy malware and steal credentials. “These campaigns
- by Francis Schmuff
- April 3, 2025
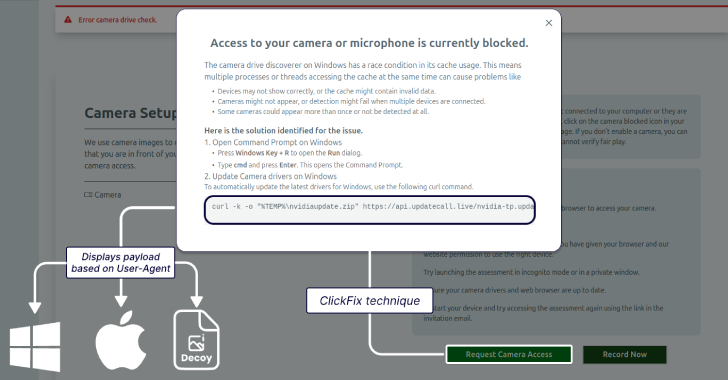
Lazarus Group Targets Job Seekers With ClickFix Tactic
The North Korean threat actors behind Contagious Interview have adopted the increasingly popular ClickFix social engineering tactic to lure job
- by Francis Schmuff
- April 3, 2025
AI Threats Are Evolving Fast — Learn Practical
The rules have changed. Again. Artificial intelligence is bringing powerful new tools to businesses. But it’s also giving cybercriminals smarter
- by Francis Schmuff
- April 3, 2025
Web 3.0 Requires Data Integrity
If you’ve ever taken a computer security class, you’ve probably learned about the three legs of computer security—confidentiality, integrity, and availability—known