As we are nearing the end of 2022, looking at the most concerning threats of this turbulent year in terms of testing numbers offers a threat-based perspective on what triggers cybersecurity teams to check how vulnerable they are to specific threats. These are the threats that were most tested to validate resilience with the Cymulate security posture management platform between January 1st and
- December 27, 2022
- by
- Cyber News, Cyber Threat Trends
- Less than a minute
- 272 Views
Related Post
- by Francis Schmuff
- May 20, 2025
KrebsOnSecurity Hit With Near-Record 6.3 Tbps DDoS
KrebsOnSecurity last week was hit by a near record distributed denial-of-service (DDoS) attack that clocked in at more than 6.3
- by Francis Schmuff
- May 20, 2025
Hazy Hawk Exploits DNS Records to Hijack CDC,
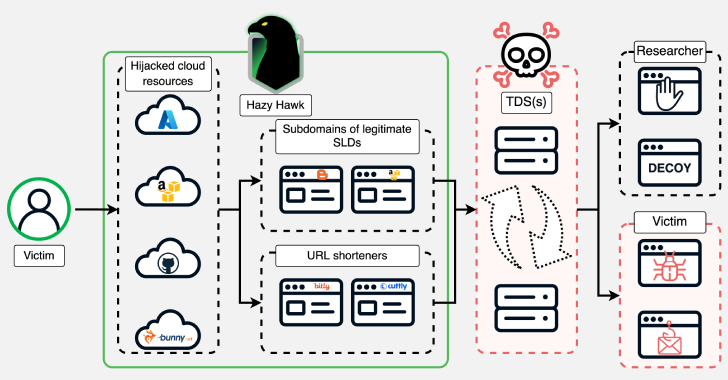
A threat actor known as Hazy Hawk has been observed hijacking abandoned cloud resources of high-profile organizations, including Amazon S3
- by Francis Schmuff
- May 20, 2025
100+ Fake Chrome Extensions Found Hijacking Sessions, Stealing
An unknown threat actor has been attributed to creating several malicious Chrome Browser extensions since February 2024 that masquerade as
- by Francis Schmuff
- May 20, 2025
The AI Fix #51: Divorce by coffee grounds,
In episode 51 of The AI Fix, a Greek man’s marriage is destroyed after ChatGPT reads his coffee, a woman