What happens when cybercriminals no longer need deep skills to breach your defenses? Today’s attackers are armed with powerful tools that do the heavy lifting — from AI-powered phishing kits to large botnets ready to strike. And they’re not just after big corporations. Anyone can be a target when fake identities, hijacked infrastructure, and insider tricks are used to slip past security

- April 28, 2025
- by Francis Schmuff
- Cyber News
- Less than a minute
- 63 Views
Related Post
- by Francis Schmuff
- May 31, 2025
New Linux Flaws Allow Password Hash Theft via
Two information disclosure flaws have been identified in apport and systemd-coredump, the core dump handlers in Ubuntu, Red Hat Enterprise
- by Francis Schmuff
- May 31, 2025
U.S. DoJ Seizes 4 Domains Supporting Cybercrime Crypting
A multinational law enforcement operation has resulted in the takedown of an online cybercrime syndicate that offered services to threat
- by CDA News Team
- May 30, 2025
Cybercrime Just Got Easier — And That Should
Cybercrime Just Got Easier — And That Should Scare You It’s never been easier to launch a cyberattack. Forget hoodie-wearing
- by Francis Schmuff
- May 30, 2025
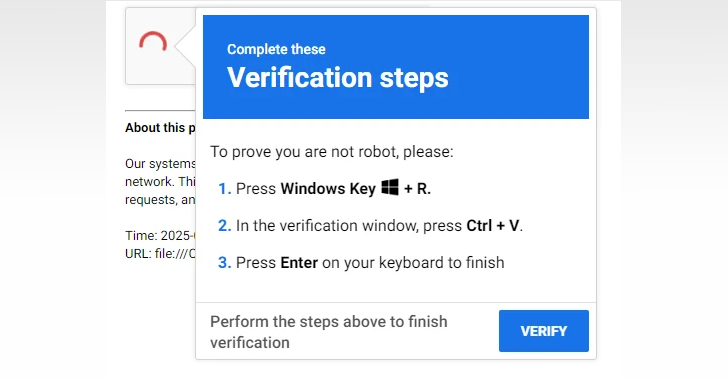
New EDDIESTEALER Malware Bypasses Chrome’s App-Bound Encryption to
A new malware campaign is distributing a novel Rust-based information stealer dubbed EDDIESTEALER using the popular ClickFix social engineering tactic